Class: RubyScep::PkiMessage
- Inherits:
-
Object
- Object
- RubyScep::PkiMessage
- Includes:
- OpenSSL::ASN1
- Defined in:
- lib/ruby_scep/pki_message.rb,
lib/ruby_scep/pki_message/degenerate.rb,
lib/ruby_scep/pki_message/signed_data.rb,
lib/ruby_scep/pki_message/enveloped_data.rb
Defined Under Namespace
Classes: Degenerate, EnvelopedData, SignedData
Constant Summary collapse
- OID_MESSAGE_TYPE =
get OID corresponding name oid-info.com/get/<the oid> get possible balues for a given OID in the CMS RFC www.ietf.org/rfc/rfc3369.txt
'2.16.840.1.113733.1.9.2'- OID_PKI_STATUS =
'2.16.840.1.113733.1.9.3'- OID_FAIL_INFO =
'2.16.840.1.113733.1.9.4'- OID_SENDER_NONCE =
'2.16.840.1.113733.1.9.5'- OID_RECIPIENT_NOUNCE =
'2.16.840.1.113733.1.9.6'- OID_TRANSACTION_ID =
'2.16.840.1.113733.1.9.7'- OID_EXTENSION_REQUEST =
'2.16.840.1.113733.1.9.8'- OID_SIGNED_DATA =
'1.2.840.113549.1.7.2'- OID_DATA =
'1.2.840.113549.1.7.1'- OID_ENVELOPED_DATA =
'1.2.840.113549.1.7.3'- OID_RSA_ENCRYPTION =
'1.2.840.113549.1.1.1'- OID_DES_ALGO =
'1.2.840.113549.3.7'- OID_CONTENT_TYPE =
'1.2.840.113549.1.9.3'- OID_SIGNING_TIME =
'1.2.840.113549.1.9.5'- OID_MESSAGE_DIGEST =
'1.2.840.113549.1.9.4'- OID_HASH_ALGO_IDENTIFIER =
'1.3.14.3.2.26'- SCEP_MESSAGE_TYPES =
complete list of possible SCEP values can be found in CISCO’s documentation www.cisco.com/c/en/us/support/docs/security-vpn/public-key-infrastructure-pki/116167-technote-scep-00.html
{ 'PKCSReq' => 19, 'CertRep' => 3, 'GetCertInitial' => 20, 'GetCert' => 21, 'GetCRL' => 22 }
- SCEP_PKI_STATUSES =
{ 'SUCCESS' => 0, 'FAILURE' => 2, 'PENDING' => 3 }
- SCEP_FAIL_INFOS =
{ 'badAlg' => 0, 'badMessageCheck' => 1, 'badRequest' => 2, 'badTime' => 3, 'badCertId' => 4 }
Instance Attribute Summary collapse
-
#p7 ⇒ Object
Returns the value of attribute p7.
Instance Method Summary collapse
-
#build_enrollment_response(csr) ⇒ Object
We are building a SCEP Secure Message Object with a valid PKCS7 structure, as referenced in tools.ietf.org/html/draft-nourse-scep-23#section-3 To see a graphical representation of the final PKCS7 structure, go to
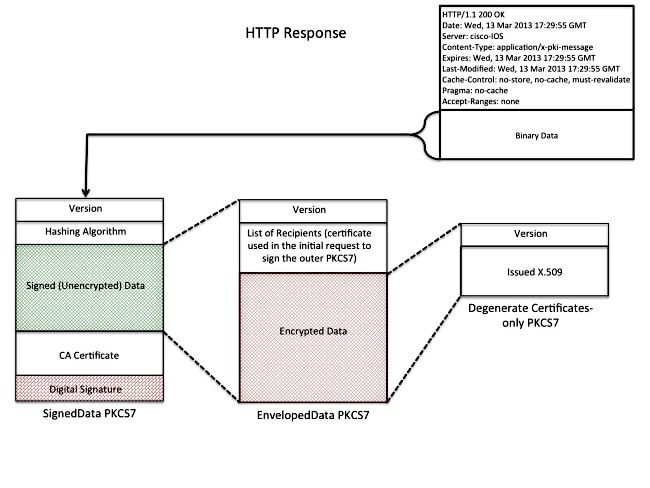 Structure: 1.
Structure: 1. -
#initialize(asn1, p7) ⇒ PkiMessage
constructor
A new instance of PkiMessage.
Constructor Details
#initialize(asn1, p7) ⇒ PkiMessage
Returns a new instance of PkiMessage.
35 36 37 38 39 40 41 |
# File 'lib/ruby_scep/pki_message.rb', line 35 def initialize(asn1, p7) signed_attributes = retrieve_signed_attributes(asn1) @message_type = SCEP_MESSAGE_TYPES.key(signed_attributes[OID_MESSAGE_TYPE].to_i) @transaction_id = signed_attributes[OID_TRANSACTION_ID] @sender_nonce = signed_attributes[OID_SENDER_NONCE] @p7 = p7 end |
Instance Attribute Details
#p7 ⇒ Object
Returns the value of attribute p7.
33 34 35 |
# File 'lib/ruby_scep/pki_message.rb', line 33 def p7 @p7 end |
Instance Method Details
#build_enrollment_response(csr) ⇒ Object
We are building a SCEP Secure Message Object with a valid PKCS7 structure, as referenced
in https://tools.ietf.org/html/draft-nourse-scep-23#section-3
To see a graphical representation of the final PKCS7 structure, go to
https://www.cisco.com/c/dam/en/us/support/docs/security-vpn/public-key-infrastructure-pki/116167-technote-scep-00-01.jpeg
Structure:
1. degenerate
a. version
b. x509
2. enveloped data
a. version
b. list of recepients
c. encrypted data (aka 1. degenerate)
3. signed data
a. version
b. hashing algo
c. signed (unencrypted) data (aka 2. enveloped data)
d. ca certificate
e. digital signature
61 62 63 64 65 |
# File 'lib/ruby_scep/pki_message.rb', line 61 def build_enrollment_response(csr) degenerate_sequence = build_degenerate_sequence(csr) enveloped_data_sequence = build_enveloped_data_sequence(degenerate_sequence) build_signed_data_sequence(enveloped_data_sequence) end |